Obiettivi | Certificazione | Contenuti | Tipologia | Prerequisiti | Durata e Frequenza | Docenti | Modalità di Iscrizione | Calendario

Il Corso Palo Alto PCNSA – Network Security Administrator anche denominato Firewall Essentials: Configuration and Management EDU-210 è un programma formativo che copre diversi aspetti della sicurezza informatica, inclusi argomenti come la configurazione avanzata di firewall, la prevenzione di minacce, il filtraggio URL, l’analisi di WildFire e la gestione dei log. I partecipanti acquisiranno competenze pratiche nell’implementazione di queste tecnologie per proteggere le reti da attacchi e minacce. Il corso si focalizza anche sul rafforzamento delle politiche di sicurezza e sulla risposta agli incidenti di sicurezza. Il Corso contribuisce alla preparazione dell’esame di Certificazione Palo Alto PCNSA – Network Security administrator.
Contattaci ora per ricevere tutti i dettagli e per richiedere, senza alcun impegno, di parlare direttamente con uno dei nostri Docenti (Clicca qui)
oppure chiamaci subito al nostro Numero Verde (800-177596)
Obiettivi del corso
Di seguito una sintesi degli obiettivi principali del Corso Palo Alto PCNSA – Network Security Administrator:
- Approfondire la comprensione delle tecnologie firewall di nuova generazione, come App-ID, Content-ID, e User-ID.
- Sviluppare abilità nella configurazione di politiche di sicurezza e NAT.
- Esplorare il filtraggio URL e le tecniche di prevenzione delle minacce.
- Approfondire le strategie di monitoraggio e reporting del traffico di rete.
- Ampliare la conoscenza sulle migliori pratiche di sicurezza per le reti.
Certificazione del corso
Esame PCNSA – Palo Alto Networks Certified Network Security Administrator; Questo esame si concentra su competenze chiave per la gestione di sistemi di sicurezza next-generation firewalls di Palo Alto Networks. Il candidato che supera questo esame dimostra abilità nell’implementare efficacemente i firewall, abilitando il traffico basato su utenti, applicazioni, politiche temporali e contenuti. Include argomenti come Next-Generation Security Platform and Architecture, Firewall Configuration, Security and NAT Policies, App-ID, Content-ID, User-ID, URL Filtering, Monitoring and Reporting, e Security Best Practices
Contenuti del corso
Cybersecurity Infrastructure and Configuration
Module 1 – Security Architecture Planning Resources
- Security platform overview
- Next-generation firewall architecture
- Zero Trust security model
- Firewall offerings
Module 2 – Infrastructure Device Configuration
- Security zones and interfaces
- Tap interfaces
- Virtual Wire interfaces
- Layer 2 interfaces
- Layer 3 interfaces
- Virtual routers
- Vlan interfaces
- Loopback interfaces
- Policy-based forwarding
Module 3 – Cybersecurity Policy
- Security policy fundamental concepts
- Security policy administration
- Network Address Translation
- Source NAT configuration
- Destination NAT configuration
Module 4 – Application Software Identification
- Application Identification (App-ID) overview
- Using App-ID in a Security policy
- Identifying unknown application traffic
- Updating App-ID
Module 5 – Anti-Virus, Anti-Spyware, and File-Blocking
- Content-ID overview
- Vulnerability Protection Security Profiles
- Antivirus Security Profiles
- Anti-Spyware Security Profiles
- File Blocking Profiles
- Attaching Security Profiles to Security policy rules
- Telemetry and threat intelligence
- Denial of service protection
Module 6 – Uniform Resource Locator Filtering
-
- URL Filtering Security Profiles
- Attaching URL Filtering Profiles
Cybersecurity Prevention and Countermeasures
Module 1 – Decryption and Certificate Management
- Decryption concepts
- Certificate management
- SSL forward proxy decryption
- SSL inbound inspection
- Other decryption topics
Module 2 – Virus Analysis and Mitigation
- Wildfire Virus Analysis and Mitigation
- Wildfire: concepts, configuring, managing, and reporting
Module 3 – End User Identification
- User-ID overview
- User mapping methods overview
- Configuring User-ID
- PAN-OS® integrated agent configuration
- Windows-based agent configuration
- Configuring group mapping
- User-ID and security policy
Module 4 – Remote Access Security
- Preparing the firewall for GlobalProtect
- Configuring the GlobalProtect portal
- Configuring the GlobalProtect gateway
- Configuring GlobalProtect agents
- Site to Site VPN Overview
- Configuring Site to Site tunnels
- IPsec troubleshooting
Module 5 – Security Monitoring and Reporting
- Dashboard, ACC, and monitor
- Log forwarding
- Syslog
- Configuring SNMP
Module 6 – Security Device High Availability
- High Availability Components and Operation
- Active/Passive HA Configuration
- Monitoring HA State
Tipologia
Corso di Formazione con Docente
Docenti
I docenti sono Istruttori accreditati Palo Alto e certificati in altre tecnologie IT, con anni di esperienza pratica nel settore e nella Formazione.
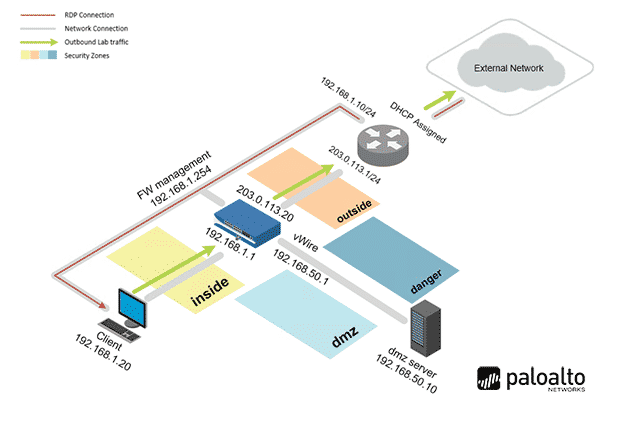
Infrastruttura laboratoriale
Per tutte le tipologie di erogazione, il Corsista può accedere alle attrezzature e ai sistemi reali Cisco presenti nei Nostri laboratori o direttamente presso i data center Cisco in modalità remota h24. Ogni partecipante dispone di un accesso per implementare le varie configurazioni avendo così un riscontro pratico e immediato della teoria affrontata. Ecco di seguito alcune topologie di rete dei Laboratori Cisco Disponibili:
Dettagli del corso
Prerequisiti
Competenze basilari in ambito Networking.
Durata del corso
- Durata Estensiva 36 Ore;
- Durata Intensiva 5gg;
Frequenza
Varie tipologie di Frequenza Estensiva ed Intensiva.
Date del corso
- Corso Palo Alto PCNSA (Formula Intensiva) – Su richiesta – 9:00 – 17:00
- Corso Palo Alto PCNSA (Formula Estensiva) – Su richiesta
Modalità di iscrizione
Le iscrizioni sono a numero chiuso per garantire ai tutti i partecipanti un servizio eccellente.
L’iscrizione avviene richiedendo di essere contattati dal seguente Link, o contattando la sede al numero verde 800-177596 o inviando una richiesta all’email [email protected].


