Obiettivi | Certificazione | Contenuti | Tipologia | Prerequisiti | Durata e Frequenza | Docenti | Modalità di Iscrizione | Calendario

Il Corso SC-200 Microsoft Security Operations Analyst mira a formare partecipanti nell’analisi delle operazioni di sicurezza per le soluzioni Microsoft. Il corso copre temi come il monitoraggio, la rilevazione e la risposta alle minacce, la gestione delle vulnerabilità e l’analisi delle informazioni sulla sicurezza, utilizzando strumenti come Microsoft Azure Sentinel e Microsoft 365 Defender. Il programma del corso si estende oltre il monitoraggio e la rilevazione delle minacce, includendo approfondimenti sulla risposta a incidenti di sicurezza e la gestione delle vulnerabilità. Il Corso contribuisce alla preparazione dell’esame di Certificazione Microsoft Security Operations Analyst Associate.
Contattaci ora per ricevere tutti i dettagli e per richiedere, senza alcun impegno, di parlare direttamente con uno dei nostri Docenti (Clicca qui)
oppure chiamaci subito al nostro Numero Verde (800-177596)
Obiettivi del corso
Di seguito una sintesi degli obiettivi principali del Corso Microsoft Security Operations Analyst SC-200:
- Approfondire la conoscenza nell’analisi delle operazioni di sicurezza.
- Utilizzare Microsoft Azure Sentinel e Microsoft 365 Defender.
- Gestire il monitoraggio, la rilevazione e la risposta alle minacce.
- Gestire le vulnerabilità e analizzare le informazioni sulla sicurezza.
- Applicare le best practice nella sicurezza delle operazioni Microsoft.
Certificazione del corso
Esame SC-200 Microsoft Security Operations Analyst; Questo esame mira a valutare le competenze dei candidati nell’analisi delle operazioni di sicurezza in ambienti multicloud, utilizzando strumenti come Microsoft Sentinel, Microsoft Defender for Cloud, e Microsoft 365 Defender. L’esame copre aree quali la mitigazione delle minacce con Microsoft 365 Defender, la gestione della postura di sicurezza cloud con Defender for Cloud, e l’uso di Microsoft Sentinel per il design, la configurazione, e la gestione della sicurezza delle informazioni. I candidati dovrebbero essere esperti in Microsoft 365, servizi cloud di Azure, e sistemi operativi Windows e Linux.
Contenuti del corso
Mitigate threats to the Microsoft 365 environment by using Microsoft 365 Defender
- Investigate, respond, and remediate threats to Microsoft Teams, SharePoint Online, and OneDrive
- Investigate, respond, and remediate threats to email by using Microsoft Defender for Office 365
- Investigate and respond to alerts generated by data loss prevention (DLP) policies
- Investigate and respond to alerts generated by insider risk policies
- Discover and manage apps by using Microsoft Defender for Cloud Apps
- Identify, investigate, and remediate security risks by using Defender for Cloud Apps
Mitigate endpoint threats by using Microsoft Defender for Endpoint
- Manage data retention, alert notification, and advanced features
- Recommend attack surface reduction (ASR) for devices
- Respond to incidents and alerts
- Configure and manage device groups
- Identify devices at risk by using the Microsoft Defender Vulnerability Management
- Manage endpoint threat indicators
- Identify unmanaged devices by using device discovery
Mitigate identity threats
- Mitigate security risks related to events for Microsoft Entra ID
- Mitigate security risks related to Microsoft Entra Identity Protection events
- Mitigate security risks related to Active Directory Domain Services (AD DS) by using Microsoft Defender for Identity
Manage extended detection and response (XDR) in Microsoft 365 Defender
- Manage incidents and automated investigations in the Microsoft 365 Defender portal
- Manage actions and submissions in the Microsoft 365 Defender portal
- Identify threats by using Kusto Query Language (KQL)
- Identify and remediate security risks by using Microsoft Secure Score
- Analyze threat analytics in the Microsoft 365 Defender portal
- Configure and manage custom detections and alerts
Investigate threats by using audit features in Microsoft 365 Defender and Microsoft Purview
- Perform threat hunting by using unified audit log
- Perform threat hunting by using Content Search
- Use the guided hunting mode in Microsoft 365 Defender
- Use the advanced hunting mode in Microsoft 365 Defender
Implement and maintain cloud security posture management
- Assign and manage regulatory compliance policies, including Microsoft cloud security benchmark (MCSB)
- Improve the Microsoft Defender for Cloud secure score by applying recommended remediations
- Configure plans and agents for Microsoft Defender for Servers
- Configure and manage Microsoft Defender for DevOps
- Configure and manage Microsoft Defender External Attack Surface Management (EASM)
Configure environment settings in Microsoft Defender for Cloud
- Plan and configure Microsoft Defender for Cloud settings, including selecting target subscriptions and workspaces
- Configure Microsoft Defender for Cloud roles
- Assess and recommend cloud workload protection
- Enable plans for Microsoft Defender for Cloud
- Configure automated onboarding of Azure resources
- Connect compute resources by using Azure Arc
- Connect multi-cloud resources by using Environment settings
Respond to alerts and incidents in Microsoft Defender for Cloud
- Set up email notifications
- Create and manage alert suppression rules
- Design and configure workflow automation in Microsoft Defender for Cloud
- Remediate alerts and incidents by using Microsoft Defender for Cloud recommendations
- Manage security alerts and incidents
- Analyze Microsoft Defender for Cloud threat intelligence reports
Design and configure a Microsoft Sentinel workspace
- Plan a Microsoft Sentinel workspace
- Configure Microsoft Sentinel roles
- Design and configure Microsoft Sentinel data storage, including log types and log retention
Plan and implement the use of data connectors for ingestion of data sources in Microsoft Sentinel
- Identify data sources to be ingested for Microsoft Sentinel
- Configure and use Microsoft Sentinel connectors for Azure resources, including Azure Policy and diagnostic settings
- Configure Microsoft Sentinel connectors for Microsoft 365 Defender and Defender for Cloud
- Design and configure Syslog and Common Event Format (CEF) event collections
- Design and configure Windows security event collections
- Configure threat intelligence connectors
- Create custom log tables in the workspace to store ingested data
Manage Microsoft Sentinel analytics rules
- Configure the Fusion rule
- Configure Microsoft security analytics rules
- Configure built-in scheduled query rules
- Configure custom scheduled query rules
- Configure near-real-time (NRT) analytics rules
- Manage analytics rules from Content hub
- Manage and use watchlists
- Manage and use threat indicators
Perform data classification and normalization
- Classify and analyze data by using entities
- Query Microsoft Sentinel data by using Advanced Security Information Model (ASIM) parsers
- Develop and manage ASIM parsers
Configure security orchestration automated response (SOAR) in Microsoft Sentinel
- Create and configure automation rules
- Create and configure Microsoft Sentinel playbooks
- Configure analytic rules to trigger automation rules
- Trigger playbooks from alerts and incidents
Manage Microsoft Sentinel incidents
- Configure an incident generation
- Triage incidents in Microsoft Sentinel
- Investigate incidents in Microsoft Sentinel
- Respond to incidents in Microsoft Sentinel
- Investigate multi-workspace incidents
Use Microsoft Sentinel workbooks to analyze and interpret data
- Activate and customize Microsoft Sentinel workbook templates
- Create custom workbooks
- Configure advanced visualizations
Hunt for threats by using Microsoft Sentinel
- Analyze attack vector coverage by using MITRE ATT&CK in Microsoft Sentinel
- Customize content gallery hunting queries
- Create custom hunting queries
- Use hunting bookmarks for data investigations
- Monitor hunting queries by using Livestream
- Retrieve and manage archived log data
- Create and manage search jobs
Manage threats by using User and Entity Behavior Analytics
- Configure User and Entity Behavior Analytics settings
- Investigate threats by using entity pages
- Configure anomaly detection analytics rules
Tipologia
Corso di Formazione con Docente
Docenti
I docenti sono Istruttori Autorizzati Microsoft e in altre tecnologie IT, con anni di esperienza pratica nel settore e nella Formazione.
Infrastruttura laboratoriale
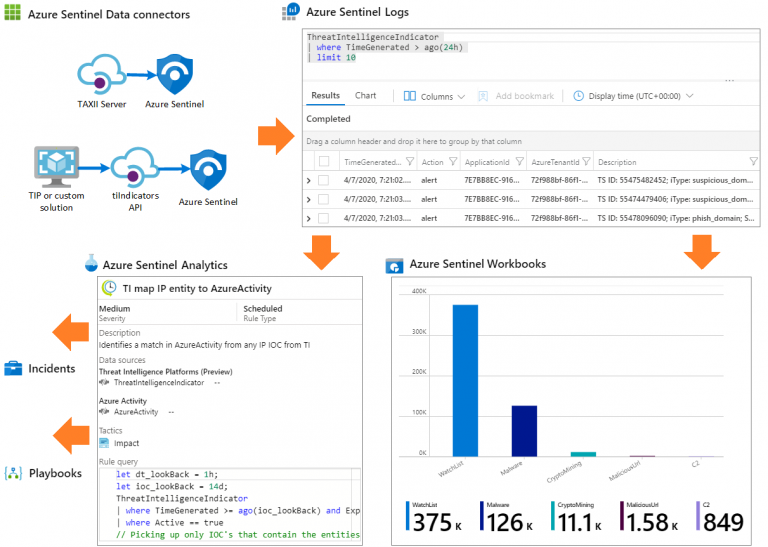
Per tutte le tipologie di erogazione, il Corsista può accedere alle attrezzature e ai sistemi presenti nei Nostri laboratori o direttamente presso i data center del Vendor o dei suoi provider autorizzati in modalità remota h24. Ogni partecipante dispone di un accesso per implementare le varie configurazioni avendo così un riscontro pratico e immediato della teoria affrontata. Ecco di seguito alcuni scenari tratti dalle attività laboratoriali:
Dettagli del corso
Prerequisiti
Si consiglia la partecipazione al Corso Microsoft Security, Compliance, and Identity Fundamentals (SC-900).
Durata del corso
- Durata Intensiva 4gg;
Frequenza
Varie tipologie di Frequenza Estensiva ed Intensiva.
Date del corso
- Corso Microsoft Security Operations Analyst (Formula Intensiva) – 02/12/2024 – 09:00 – 17:00
Modalità di iscrizione
Le iscrizioni sono a numero chiuso per garantire ai tutti i partecipanti un servizio eccellente.
L’iscrizione avviene richiedendo di essere contattati dal seguente Link, o contattando la sede al numero verde 800-177596 o inviando una richiesta all’email [email protected].


