Obiettivi | Certificazione | Contenuti | Tipologia | Prerequisiti | Durata e Frequenza | Docenti | Modalità di Iscrizione | Calendario

Il Corso AZ-500 Azure Security Technologies è progettato per partecipanti interessati a una profonda comprensione delle tecnologie di sicurezza di Azure. I partecipanti apprenderanno a proteggere dati, applicazioni e infrastrutture in Azure utilizzando strumenti di sicurezza avanzati. Il corso copre gestione degli accessi, protezione delle identità, gestione delle chiavi, e sicurezza delle reti. Saranno in grado di implementare misure di sicurezza, rilevare e rispondere a minacce di sicurezza e gestire la conformità. Il Corso contribuisce alla preparazione dell’esame di Certificazione Azure Security Engineer Associate.
Contattaci ora per ricevere tutti i dettagli e per richiedere, senza alcun impegno, di parlare direttamente con uno dei nostri Docenti (Clicca qui)
oppure chiamaci subito al nostro Numero Verde (800-177596)
Obiettivi del corso
Di seguito una sintesi degli obiettivi principali del Corso Azure Security Technologies AZ-500:
- Protezione dei dati e delle applicazioni in Azure.
- Gestione degli accessi e identità in Azure.
- Implementazione della sicurezza delle reti.
- Uso di Azure Key Vault e Azure Sentinel.
- Gestione delle minacce e conformità alle normative.
Certificazione del corso
Esame AZ-500 Microsoft Azure Security Technologies; Questo esame valuta le competenze di un candidato nell’implementare, gestire e monitorare la sicurezza in ambienti Azure, multi-cloud e ibridi. I contenuti dell’esame si concentrano su quattro aree principali: gestione dell’identità e dell’accesso, sicurezza di rete, sicurezza di calcolo, storage e database, e gestione delle operazioni di sicurezza. Il candidato deve dimostrare conoscenza nella protezione di identità, dati, applicazioni e reti, oltre a competenze nel mitigare vulnerabilità e rispondere a incidenti di sicurezza.
Contenuti del corso
Manage identities in Microsoft Entra ID
- Secure users in Microsoft Entra ID
- Secure groups in Microsoft Entra ID
- Recommend when to use external identities
- Secure external identities
- Implement Microsoft Entra ID Protection
Manage authentication by using Microsoft Entra ID
- Configure Microsoft Entra Verified ID
- Implement multi-factor authentication (MFA)
- Implement passwordless authentication
- Implement password protection
- Implement single sign-on (SSO)
- Integrate single sign on (SSO) and identity providers
- Recommend and enforce modern authentication protocols
Manage authorization by using Microsoft Entra ID
- Configure Azure role permissions for management groups, subscriptions, resource groups, and resources
- Assign built-in roles in Microsoft Entra ID
- Assign built-in roles in Azure
- Create and assign custom roles, including Azure roles and Microsoft Microsoft Entra roles
- Implement and manage Microsoft Entra Permissions Management
- Configure Microsoft Entra Privileged Identity Management (PIM)
- Configure role management and access reviews in Microsoft Entra
- Implement Conditional Access policies
Manage application access in Microsoft Entra ID
- Manage access to enterprise applications in Microsoft Entra ID, including OAuth permission grants
- Manage app registrations in Microsoft Entra ID
- Configure app registration permission scopes
- Manage app registration permission consent
- Manage and use service principals
- Manage managed identities for Azure resources
- Recommend when to use and configure a Microsoft Entra Application Proxy, including authentication
Plan and implement security for virtual networks
- Plan and implement Network Security Groups (NSGs) and Application Security Groups (ASGs)
- Plan and implement user-defined routes (UDRs)
- Plan and implement Virtual Network peering or VPN gateway
- Plan and implement Virtual WAN, including secured virtual hub
- Secure VPN connectivity, including point-to-site and site-to-site
- Implement encryption over ExpressRoute
- Configure firewall settings on PaaS resources
- Monitor network security by using Network Watcher, including NSG flow logging
Plan and implement security for private access to Azure resources
- Plan and implement virtual network Service Endpoints
- Plan and implement Private Endpoints
- Plan and implement Private Link services
- Plan and implement network integration for Azure App Service and Azure Functions
- Plan and implement network security configurations for an App Service Environment (ASE)
- Plan and implement network security configurations for an Azure SQL Managed Instance
Plan and implement security for public access to Azure resources
- Plan and implement Transport Layer Security (TLS) to applications, including Azure App Service and API Management
- Plan, implement, and manage an Azure Firewall, including Azure Firewall Manager and firewall policies
- Plan and implement an Azure Application Gateway
- Plan and implement an Azure Front Door, including Content Delivery Network (CDN)
- Plan and implement a Web Application Firewall (WAF)
- Recommend when to use Azure DDoS Protection Standard
Plan and implement advanced security for compute
- Plan and implement remote access to public endpoints, including Azure Bastion and just-in-time (JIT) virtual machine (VM) access
- Configure network isolation for Azure Kubernetes Service (AKS)
- Secure and monitor AKS
- Configure authentication for AKS
- Configure security monitoring for Azure Container Instances (ACIs)
- Configure security monitoring for Azure Container Apps (ACAs)
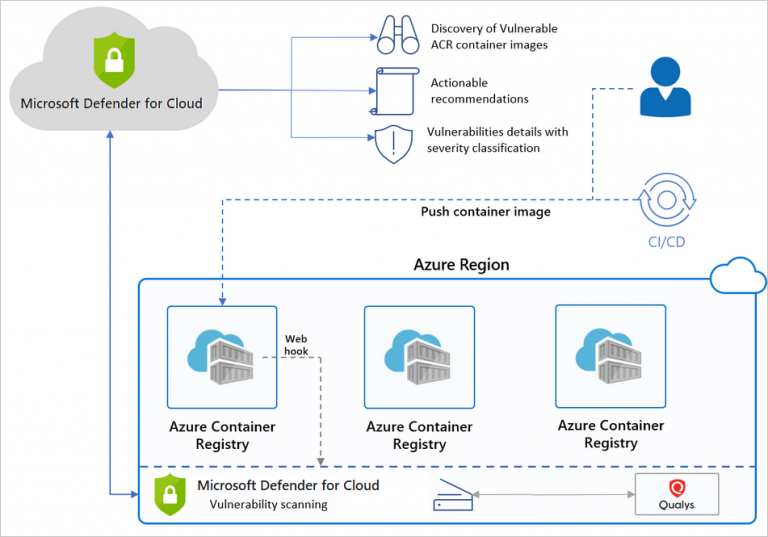
- Manage access to Azure Container Registry (ACR)
- Configure disk encryption, including Azure Disk Encryption (ADE), encryption as host, and confidential disk encryption
- Recommend security configurations for Azure API Management
Plan and implement security for storage
- Configure access control for storage accounts
- Manage life cycle for storage account access keys
- Select and configure an appropriate method for access to Azure Files
- Select and configure an appropriate method for access to Azure Blob Storage
- Select and configure an appropriate method for access to Azure Tables
- Select and configure an appropriate method for access to Azure Queues
- Select and configure appropriate methods for protecting against data security threats, including soft delete, backups, versioning, and immutable storage
- Configure Bring your own key (BYOK)
- Enable double encryption at the Azure Storage infrastructure level
Plan and implement security for Azure SQL Database and Azure SQL Managed Instance
- Enable database authentication by using Microsoft Entra ID
- Enable database auditing
- Identify use cases for the Microsoft Purview governance portal
- Implement data classification of sensitive information by using the Microsoft Purview governance portal
- Plan and implement dynamic masking
- Implement Transparent Database Encryption (TDE)
- Recommend when to use Azure SQL Database Always Encrypted
Plan, implement, and manage governance for security
- Create, assign, and interpret security policies and initiatives in Azure Policy
- Configure security settings by using Azure Blueprint
- Deploy secure infrastructures by using a landing zone
- Create and configure an Azure Key Vault
- Recommend when to use a dedicated Hardware Security Module (HSM)
- Configure access to Key Vault, including vault access policies and Azure Role Based Access Control
- Manage certificates, secrets, and keys
- Configure key rotation
- Configure backup and recovery of certificates, secrets, and keys
Manage security posture by using Microsoft Defender for Cloud
- Identify and remediate security risks by using the Microsoft Defender for Cloud Secure Score and Inventory
- Assess compliance against security frameworks and Microsoft Defender for Cloud
- Add industry and regulatory standards to Microsoft Defender for Cloud
- Add custom initiatives to Microsoft Defender for Cloud
- Connect hybrid cloud and multi-cloud environments to Microsoft Defender for Cloud
- Identify and monitor external assets by using Microsoft Defender External Attack Surface Management
Configure and manage threat protection by using Microsoft Defender for Cloud
- Enable workload protection services in Microsoft Defender for Cloud, including Microsoft Defender for Storage, Databases, Containers, App Service, Key Vault, Resource Manager, and DNS
- Configure Microsoft Defender for Servers
- Configure Microsoft Defender for Azure SQL Database
- Manage and respond to security alerts in Microsoft Defender for Cloud
- Configure workflow automation by using Microsoft Defender for Cloud
- Evaluate vulnerability scans from Microsoft Defender for Server
Configure and manage security monitoring and automation solutions
- Monitor security events by using Azure Monitor
- Configure data connectors in Microsoft Sentinel
- Create and customize analytics rules in Microsoft Sentinel
- Evaluate alerts and incidents in Microsoft Sentinel
- Configure automation in Microsoft Sentinel
Tipologia
Corso di Formazione con Docente
Docenti
I docenti sono Istruttori Autorizzati Microsoft e in altre tecnologie IT, con anni di esperienza pratica nel settore e nella Formazione.
Infrastruttura laboratoriale
Per tutte le tipologie di erogazione, il Corsista può accedere alle attrezzature e ai sistemi presenti nei Nostri laboratori o direttamente presso i data center del Vendor o dei suoi provider autorizzati in modalità remota h24. Ogni partecipante dispone di un accesso per implementare le varie configurazioni avendo così un riscontro pratico e immediato della teoria affrontata. Ecco di seguito alcuni scenari tratti dalle attività laboratoriali:
Dettagli del corso
Prerequisiti
Si consiglia la partecipazione al Corso Azure Administrator.
Durata del corso
- Durata Intensiva 4gg;
Frequenza
Varie tipologie di Frequenza Estensiva ed Intensiva.
Date del corso
- Corso Azure Security Technologies (Formula Intensiva) – 14/10/2024 – 09:00 – 17:00
Modalità di iscrizione
Le iscrizioni sono a numero chiuso per garantire ai tutti i partecipanti un servizio eccellente.
L’iscrizione avviene richiedendo di essere contattati dal seguente Link, o contattando la sede al numero verde 800-177596 o inviando una richiesta all’email [email protected].


