Obiettivi | Certificazione | Contenuti | Tipologia | Prerequisiti | Durata e Frequenza | Docenti | Modalità di Iscrizione | Calendario

Il Corso SCOR Implementing and Operating Cisco Security Core Technologies rappresenta il pilastro fondamentale del percorso tecnologico e di certificazione Security e prepara il partecipante all’esame Core della Certificazione CCNP Security (Esame 350-701). Il corso ha come obiettivo principale fornire ai partecipanti le conoscenze e le competenze necessarie per implementare e gestire tecnologie di sicurezza Cisco in un’ampia gamma di ambienti. Durante il corso, i partecipanti acquisiranno una comprensione approfondita dei principi e delle tecniche di sicurezza informatica, tra cui la gestione degli endpoint, la gestione delle identità e degli accessi, la gestione dei firewall e delle VPN, la gestione delle minacce avanzate e la gestione dei sistemi di sicurezza. Inoltre, i partecipanti apprenderanno a configurare e gestire tecnologie di sicurezza Cisco, come ASA, Firepower, VPN, IPS e AMP. Il Corso contribuisce alla preparazione dell’esame di Certificazione CCNP Security (Esame 350-701).
Sintesi Statistica :
- Corsi realizzati: 28;
- Numero Corsisti: 204;
- Superamento Esame: 89,20%
Contattaci ora per ricevere tutti i dettagli e per richiedere, senza alcun impegno, di parlare direttamente con uno dei nostri Docenti (Clicca qui)
oppure chiamaci subito al nostro Numero Verde (800-177596)
Obiettivi del corso
Di seguito una sintesi degli obiettivi principali del Corso SCOR Implementing and Operating Cisco Security Core Technologies:
- Fornire una comprensione approfondita dei principi di sicurezza informatica.
- Gestire e configurare tecnologie di sicurezza Cisco come ASA, Firepower e VPN.
- Acquisire competenze nella gestione delle identità e degli accessi.
- Approfondire la gestione delle minacce avanzate e dei sistemi di sicurezza.
- Prepararsi per l’esame di Certificazione CCNP Security SCOR.
Certificazione del corso
Esame 350-701 SCOR Implementing and Operating Cisco Security Core Technologies;
Esame Parte delle Certificazioni: CCNP Security, CCIE Security; Il nuovo programma di certificazione CCNP Security prepara per i ruoli professionali nelle odierne tecnologie sulla sicurezza informatica. La CCNP Security ora include elementi di automazione e programmabilità per la massima scalabilità delle moderne infrastrutture di sicurezza. In particolare l’esame 350-701 SCOR testa competenze su argomenti quali: network security, cloud security, content security, endpoint protection e detection, secure network access, visibility ed enforcements.
Contenuti del corso
- Describing Information Security Concepts
- Describing Common TCP/IP Attacks
- Describing Common Network Application Attacks
- Describing Common Endpoint Attacks*
- Describing Network Security Technologies
- Deploying Cisco ASA Firewall
- Deploying Cisco Firepower Next-Generation Firewall
- Deploying Email Content Security
- Deploying Web Content Security
- Deploying Cisco Umbrella*
- Explaining VPN Technologies and Cryptography
- Introducing Cisco Secure Site-to-Site VPN Solutions
- Deploying Cisco IOS VTI-Based Point-to-Point IPsec VPNs
- Deploying Point-to-Point IPsec VPNs on the Cisco ASA and Cisco Firepower NGFW
- Introducing Cisco Secure Remote Access VPN Solutions
- Deploying Remote Access SSL VPNs on the Cisco ASA and Cisco Firepower NGFW
- Explaining Cisco Secure Network Access Solutions
- Describing 802.1X Authentication
- Configuring 802.1X Authentication
- Describing Endpoint Security Technologies*
- Deploying Cisco Advanced Malware Protection (AMP) for Endpoints*
- Introducing Network Infrastructure Protection*
- Deploying Control Plane Security Controls*
- Deploying Layer 2 Data Plane Security Controls*
- Deploying Layer 3 Data Plane Security Controls*
- Deploying Management Plane Security Controls*
- Deploying Traffic Telemetry Methods*
- Deploying Cisco Stealthwatch Enterprise*
- Describing Cloud and Common Cloud Attacks*
- Securing the Cloud*
- Deploying Cisco Stealthwatch Cloud*
- Describing Software-Defined Networking (SDN*)
Attività Laboratoriali
- Configure Network Settings and NAT on Cisco ASA
- Configure Cisco ASA Access Control Policies
- Configure Cisco Firepower NGFW NAT
- Configure Cisco Firepower NGFW Access Control Policy
- Configure Cisco Firepower NGFW Discovery and IPS Policy
- Configure Cisco NGFW Malware and File Policy
- Configure Listener, Host Access Table (HAT), and Recipient Access Table (RAT) on Cisco Email Security Appliance (ESA)
- Configure Mail Policies
- Configure Proxy Services, Authentication, and HTTPS Decryption
- Enforce Acceptable Use Control and Malware Protection
- Examine the Umbrella Dashboard
- Examine Cisco Umbrella Investigate
- Explore DNS Ransomware Protection by Cisco Umbrella
- Configure Static VTI Point-to-Point IPsec IKEv2 Tunnel
- Configure Point-to-Point VPN between the Cisco ASA and Cisco Firepower NGFW
- Configure Remote Access VPN on the Cisco Firepower NGFW
- Explore Cisco AMP for Endpoints
- Perform Endpoint Analysis Using AMP for Endpoints Console
- Explore File Ransomware Protection by Cisco AMP for Endpoints Console
- Explore Cisco Stealthwatch Enterprise v6.9.3
- Explore Cognitive Threat Analytics (CTA) in Stealthwatch Enterprise v7.0
- Explore the Cisco Cloudlock Dashboard and User Security
- Explore Cisco Cloudlock Application and Data Security
- Explore Cisco Stealthwatch Cloud
- Explore Stealthwatch Cloud Alert Settings, Watchlists, and Sensors
Tipologia
Corso di Formazione con Docente
Docenti
I docenti sono Istruttori accreditati CISCO e certificati in altre tecnologie IT, con anni di esperienza pratica nel settore e nella Formazione.
Infrastruttura laboratoriale
Per tutte le tipologie di erogazione, il Corsista può accedere alle attrezzature e ai sistemi reali Cisco presenti nei Nostri laboratori o direttamente presso i data center Cisco in modalità remota h24. Ogni partecipante dispone di un accesso per implementare le varie configurazioni avendo così un riscontro pratico e immediato della teoria affrontata. Ecco di seguito alcune topologie di rete dei Laboratori Cisco Disponibili:
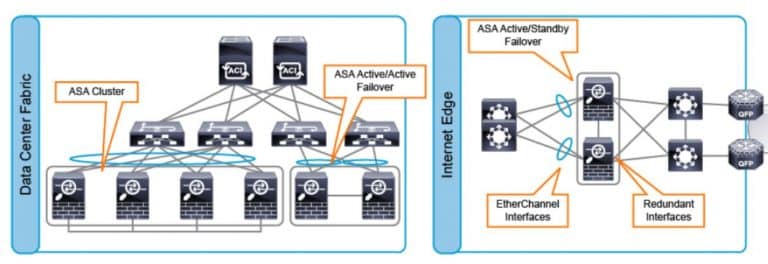
Dettagli del corso
Prerequisiti
Si consiglia la partecipazione al Corso Cisco CCNA e al Corso Cisco Cybersecurity.
Durata del corso
- Durata Estensiva 60 Ore;
- Durata Intensiva 5gg;
Frequenza
Varie tipologie di Frequenza Estensiva ed Intensiva.
Date del corso
- Corso Cisco SCOR (Formula Estensiva Serale) – 18/11/2024 – Lun. Mer. 18:30/21:30
- Corso Cisco SCOR (Formula Intensiva) – 07/10/2024- 9:00 – 17:00
Modalità di iscrizione
Le iscrizioni sono a numero chiuso per garantire ai tutti i partecipanti un servizio eccellente.
L’iscrizione avviene richiedendo di essere contattati dal seguente Link, o contattando la sede al numero verde 800-177596 o inviando una richiesta all’email [email protected].


