Obiettivi | Certificazione | Contenuti | Tipologia | Prerequisiti | Durata e Frequenza | Docenti | Modalità di Iscrizione | Calendario

Il Corso Check Point Cybersecurity Boot Camp CCSA & CCSE è un’esperienza formativa ideata per partecipanti che desiderano acquisire una solida base nelle tecnologie e soluzioni di sicurezza Check Point, oltre a perfezionare le loro competenze nel settore. Il boot camp combina i contenuti dei corsi Check Point Certified Security Administrator (CCSA) e Check Point Certified Security Expert (CCSE) in un unico intervento formativo altamente efficace. Durante il corso, i partecipanti esplorano una serie di lezioni teoriche e pratiche che coprono vari argomenti, tra cui la configurazione e la gestione dei sistemi di sicurezza Check Point, l’implementazione di politiche di sicurezza, la risoluzione dei problemi e l’utilizzo di tecnologie e strumenti avanzati. Le tecnologie trattate includono firewall, VPN, intrusion prevention system (IPS), mobile access, data loss prevention (DLP) e gestione unificata delle minacce (UTM). I partecipanti imparano come progettare, implementare e gestire soluzioni di sicurezza aziendale, nonché come identificare e risolvere problemi complessi che possono insorgere durante l’installazione e la gestione di queste soluzioni. Il corso contribuisce alla preparazione dell’esame di Certificazione Check Point CCSA e CCSE.
Contattaci ora per ricevere tutti i dettagli e per richiedere, senza alcun impegno, di parlare direttamente con uno dei nostri Docenti (Clicca qui)
oppure chiamaci subito al nostro Numero Verde (800-177596)
Obiettivi del corso
Di seguito una sintesi degli obiettivi principali del Corso Check Point Cybersecurity Boot Camp CCSA & CCSE:
- Configurare e gestire i firewall Check Point per la sicurezza della rete
- Impostare e mantenere le VPN per la sicurezza delle connessioni remote
- Applicare e gestire l’intrusion prevention system (IPS) per prevenire gli attacchi
- Implementare soluzioni di mobile access e data loss prevention (DLP)
- Gestire la sicurezza complessiva tramite l’approccio di gestione unificata delle minacce (UTM)
Certificazione del corso
- Esame Check Point Security Administrator (CCSA); Questo esame è una valutazione rigorosa, destinata a candidati che desiderano dimostrare la loro competenza nelle tecnologie e nelle pratiche di sicurezza Check Point. Questo esame testa la conoscenza approfondita dei partecipanti in vari aspetti chiave della sicurezza informatica, con un focus particolare sulle soluzioni Check Point. I candidati sono valutati sulla loro abilità di configurare e gestire la sicurezza di rete utilizzando il software Check Point, inclusa l’installazione e la configurazione di firewall e VPN. Altri argomenti cruciali includono la gestione degli utenti e degli oggetti di sicurezza, la configurazione delle regole di sicurezza e del controllo degli accessi, nonché la capacità di identificare e rispondere a minacce informatiche. Superare questo esame conferma che il candidato possiede le competenze necessarie per amministrare efficacemente le soluzioni di sicurezza Check Point in un ambiente professionale.
- Esame Check Point Certified Security Expert (CCSE); Questo esame è una valutazione approfondita per i candidati che desiderano dimostrare la loro competenza avanzata nelle soluzioni di sicurezza Check Point. Questo esame mette alla prova la capacità dei candidati di configurare e gestire firewall avanzati, VPN, e sistemi di prevenzione delle intrusioni (IPS). Inoltre, i partecipanti sono testati sulla loro abilità nell’implementare soluzioni di accesso mobile e strategie di prevenzione della perdita di dati (DLP), nonché nella gestione di Unified Threat Management (UTM). L’esame richiede anche una comprensione approfondita dell’ottimizzazione e della risoluzione dei problemi in ambienti di sicurezza complessi. Superare questo esame conferma che il candidato possiede le competenze necessarie per operare efficacemente come un esperto di sicurezza nell’ambito delle tecnologie Check Point.
Contenuti del corso
- Describe the primary components of a Check Point Three-Tier Architecture and explain how they work together in the Check Point environment.
- Identify the basic workflow to install Security Management Server and Security Gateway for a single-domain solution.
- Create SmartConsole objects that correspond to the organization’s topology for use in policies and rules.
- Identify the tools available to manage Check Point licenses and contracts, including their purpose and use.
- Identify features and capabilities that enhance the configuration and management of the Security Policy.
- Demonstrate an understanding of Application Control & URL Filtering and Autonomous Threat Prevention capabilities and how to configure these solutions to meet an organization’s security requirements.
- Describe how to analyze and interpret VPN tunnel traffic.
- Identify how to monitor the health of supported Check Point hardware using the Gaia Portal and the command line.
- Describe the different methods for backing up Check Point system information and discuss best practices and recommendations for each method.
- Identify the types of technologies that Check Point supports for automation.
- Explain the purpose of the Check Management High Availability (HA) deployment.
- Explain the basic concepts of Clustering and ClusterXL, including protocols, synchronization, and connection stickiness.
- Explain the purpose of dynamic objects, updatable objects, and network feeds.
- Describe the Identity Awareness components and configurations.
- Describe different Check Point Threat Prevention solutions.
- Articulate how the Intrusion Prevention System is configured.
- Explain the purpose of Domain-based VPNs.
- Describe situations where externally managed certificate authentication is used.
- Describe how client security can be provided by Remote Access.
- Discuss the Mobile Access Software Blade.
- Define performance tuning solutions and basic configuration workflow.
- Identify supported upgrade methods and procedures for Security Gateways.
Attività Laboratoriali
- Deploy SmartConsole
- Install a Security Management Server
- Install a Security Gateway
- Configure Objects in SmartConsole
- Establish Secure Internal Communication
- Manage Administrator Access
- Manage Licenses
- Create a Security Policy
- Configure Order Layers
- Configure a Shared Inline Layer
- Configure NAT
- Integrate Security with a Unified Policy
- Elevate Security with Autonomous Threat Prevention
- Configure a Locally Managed Site-to-Site VPN
- Elevate Traffic View
- Monitor System States
- Maintain the Security Environment
- Navigate the Environment and Use the Management API
- Deploy Secondary Security Management Server
- Configure a Dedicated Log Server
- Deploy SmartEvent
- Configure a High Availability Security Gateway Cluster
- Work with ClusterXL
- Configure Dynamic and Updateable Objects
- Verify Accelerated Policy Installation and Monitoring Status
- Elevate Security with HTTPS Inspection
- Deploy Identity Awareness
- Customize Threat Prevention
- Configure a Site-to-Site VPN with an Interoperable Device
- Deploy Remote Access VPN
- Configure Mobile Access VPN
- Monitor Policy Compliance
- Report SmartEvent Statistics
- Tune Security Gateway Performance
Tipologia
Corso di Formazione con Docente
Docenti
I docenti sono Istruttori Autorizzati Check Point e in altre tecnologie IT, con anni di esperienza pratica nel settore e nella Formazione.
Infrastruttura laboratoriale
Per tutte le tipologie di erogazione, il Corsista può accedere alle attrezzature e ai sistemi presenti nei Nostri laboratori o direttamente presso i data center del Vendor o dei suoi provider autorizzati in modalità remota h24. Ogni partecipante dispone di un accesso per implementare le varie configurazioni avendo così un riscontro pratico e immediato della teoria affrontata. Ecco di seguito alcuni scenari tratti dalle attività laboratoriali:
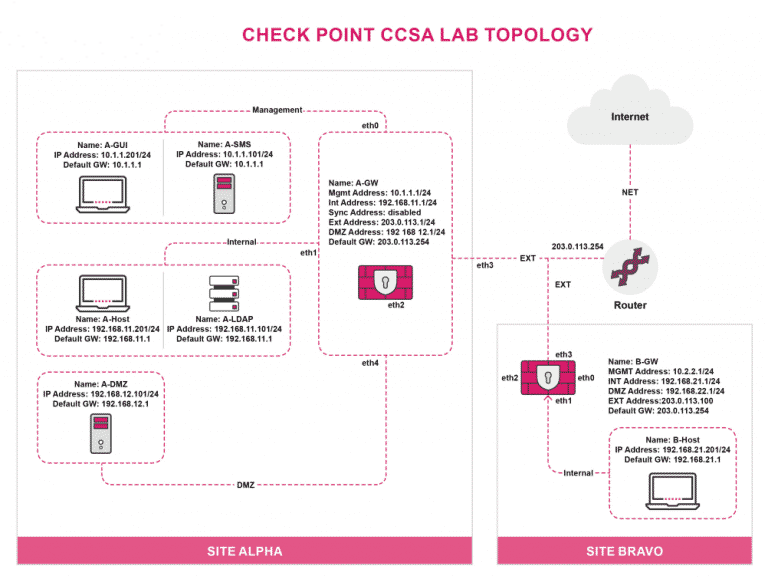
Dettagli del corso
Prerequisiti
I partecipanti dovranno avere una conoscenza basilare dei fondamenti del Networking e della sistemi Windows/Linux.
Durata del corso
- Durata Intensiva 5gg;
Frequenza
Varie tipologie di Frequenza Estensiva ed Intensiva.
Date del corso
- Corso Check Point Cybersecurity Boot Camp CCSA & CCSE (Formula Intensiva) – Su Richiesta – 9:00 – 17:00
Modalità di iscrizione
Le iscrizioni sono a numero chiuso per garantire ai tutti i partecipanti un servizio eccellente.
L’iscrizione avviene richiedendo di essere contattati dal seguente Link, o contattando la sede al numero verde 800-177596 o inviando una richiesta all’email [email protected].


