Obiettivi | Certificazione | Contenuti | Tipologia | Prerequisiti | Durata e Frequenza | Docenti | Modalità di Iscrizione | Calendario

Il Corso AWS Security Essentials (SECESS) è progettato per introdurre i partecipanti alle nozioni fondamentali sulla sicurezza su AWS. Durante il corso, i partecipanti acquisiranno competenze teoriche e pratiche sull’identificazione dei rischi, la protezione dei dati, il monitoraggio dei sistemi, e altre best practices per garantire la sicurezza delle applicazioni e dei servizi su AWS. Al termine del corso, i partecipanti saranno in grado di comprendere i principali concetti legati alla sicurezza su AWS e di applicare le best practices per creare un ambiente sicuro e protetto. Il corso contribuisce alla preparazione per la Certificazione AWS Certified Security – Specialty.
Contattaci ora per ricevere tutti i dettagli e per richiedere, senza alcun impegno, di parlare direttamente con uno dei nostri Docenti (Clicca qui)
oppure chiamaci subito al nostro Numero Verde (800-177596)
Obiettivi del corso
Di seguito una sintesi degli obiettivi principali del corso Corso AWS Security Essentials (SECESS):
- Introduzione alla Sicurezza AWS: Fornire una panoramica delle nozioni fondamentali relative alla sicurezza su AWS.
- Identificazione dei Rischi: Acquisire competenze teoriche e pratiche sull’identificazione dei rischi associati all’utilizzo di AWS.
- Protezione dei Dati: Imparare le strategie e le best practices per proteggere i dati e assicurare la loro integrità su AWS.
- Monitoraggio dei Sistemi: Acquisire conoscenze sul monitoraggio dei sistemi e delle attività su AWS per garantire la sicurezza delle applicazioni e dei servizi.
- Applicazione delle Best Practices: Essere in grado di applicare le best practices di sicurezza su AWS per creare un ambiente sicuro e protetto.
Certificazione del corso
Esame AWS Certified Security – Specialty;
L’esame di certificazione AWS Certified Security – Specialty (SCS-C02) è focalizzato sulla valutazione delle competenze avanzate dei candidati nella progettazione e nell’implementazione di soluzioni di sicurezza su AWS. L’esame tratta tematiche quali la protezione dei dati, la gestione delle identità e degli accessi, la conformità normativa e la sicurezza delle infrastrutture.
L’obiettivo principale è garantire che i candidati dimostrino una conoscenza approfondita delle best practice e delle soluzioni avanzate AWS per garantire la sicurezza delle applicazioni e delle infrastrutture. Durante l’esame, i candidati affronteranno argomenti quali la progettazione di architetture sicure, l’implementazione di controlli e politiche di sicurezza e la risposta agli incidenti di sicurezza.
Contenuti del corso
Module 1: Security on AWS
- Security design principles in the AWS Cloud
- AWS Shared Responsibility Model
Module 2: Security OF the Cloud
- AWS Global Infrastructure
- Data Center Security
- Compliance and Governance
Module 3: Security IN the Cloud – Part 1
- Identity and Access Management
- Data Protection
- Lab 01 – Introduction to Security Policies
Module 4: Security IN the Cloud – Part 2
- Securing your infrastructure
- Monitoring and detective controls
- Lab 02 – Securing VPC Resources with Security Groups
Module 5: Security IN the Cloud – Part 3
- DDoS mitigation
- Incident response essentials
- Lab 03 – Automating Incident Response with AWS Config and AWS Lambda
Module 6: Course Wrap Up
- AWS Well-Architected tool overview
Tipologia
Corso di Formazione con Docente
Docenti
I docenti sono Istruttori accreditati Amazon AWS e certificati in altre tecnologie IT, con anni di esperienza pratica nel settore e nella Formazione.
Infrastruttura laboratoriale
Per tutte le tipologie di erogazione, il Corsista può accedere alle attrezzature e ai sistemi presenti nei Nostri laboratori o direttamente presso i data center del Vendor o dei suoi provider autorizzati in modalità remota h24. Ogni partecipante dispone di un accesso per implementare le varie configurazioni avendo così un riscontro pratico e immediato della teoria affrontata. Ecco di seguito alcuni scenari tratti dalle attività laboratoriali:
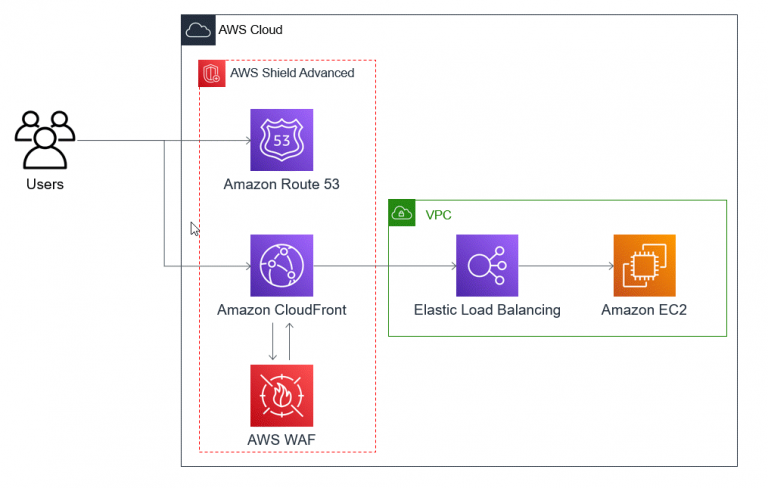
Dettagli del corso
Prerequisiti
Si consiglia la partecipazione al Corso AWS Cloud Practitioner Essentials.
Durata del corso
Durata Intensiva 1gg.
Frequenza
Varie tipologie di Frequenza Estensiva ed Intensiva.
Date del corso
- AWS Security Essentials (Formula Intensiva) – 15/05/2024 – 09:00 – 17:00
- AWS Security Essentials (Formula Intensiva) – 12/06/2024 – 09:00 – 17:00
- AWS Security Essentials (Formula Intensiva) – 10/07/2024 – 09:00 – 17:00
- AWS Security Essentials (Formula Intensiva) – 11/09/2024 – 09:00 – 17:00
- AWS Security Essentials (Formula Intensiva) – 09/10/2024 – 09:00 – 17:00
- AWS Security Essentials (Formula Intensiva) – 13/11/2024 – 09:00 – 17:00
- AWS Security Essentials (Formula Intensiva) – 11/12/2024 – 09:00 – 17:00
Modalità di iscrizione
Le iscrizioni sono a numero chiuso per garantire ai tutti i partecipanti un servizio eccellente. L’iscrizione avviene richiedendo di essere contattati dal seguente Link, o contattando la sede al numero verde 800-177596 o inviando una richiesta all’email [email protected].


