Obiettivi | Certificazione | Contenuti | Tipologia | Prerequisiti | Durata e Frequenza | Docenti | Modalità di Iscrizione | Calendario

Il Corso Cisco CCNA – Implementing and Administering Cisco Solutions consente ai partecipanti di accedere in modo pratico alle più recenti tecnologie per la gestione delle reti, nonché di prepararsi a conseguire una delle certificazioni più richieste dal mercato del lavoro, la Cisco CCNA Esame 200-301. Punto fondamentale di tutto il sistema di certificazione Cisco.
Al termine i corsisti saranno in grado di progettare e implementare e gestire:
Reti LAN attraverso tecnologie fondamentali quali VLAN, Spanning Tree Protocol, VLAN Trunk Protocol, Etherchannel, HSRP, Switch Port Analyzer etc…
Reti WAN attraverso i protocolli di Routing IPv4 e IPv6 Rip, Eigrp, Ospf, BGP nonché attraverso l’uso di tecnologie quali PPP, PPPoE, VPN, DMVPN etc…
Monitoraggio e Sicurezza attraverso NetFlow, SNMP applicando Politiche di QOS, nonché introducendo a strumenti quali ACL, Firewall etc..
Reti Wireless WLAN utilizzando le più avanzate e recenti tecnologie in quest’ambito per intercettare le esigenze delle realtà produttive medio e grandi.
Reti Programmabili passando dall’introduzione dei nuovi elementi come la Network Programmability nell’ambito del Software Defined Networking (SDN) non più come elemento teorico ma affrontando casi pratici reali.
Il tutto viene proposto su apparati di rete Cisco, ma le trattazioni hanno carattere universale e sono applicabili a contesti di altri Produttori. La Metodologia didattica su cui il corso si basa sfrutta le più moderne tecnologie di apprendimento, con l’utilizzo di innovativi strumenti che aiutano a gestire ogni aspetto del corso, arricchendo le tradizionali lezioni teorico – pratiche con tecniche utili a ridurre drasticamente i tempi di apprendimento. Il corso presenta una forte componente Pratica , realizzata attraverso laboratori reali appositamente organizzati secondo direttive Cisco. Il corsista può accedere ai laboratori in maniera H24 e da ogni postazione dotata di una connessione a internet e per tutta la durata del corso.
Sintesi Statistica :
- Corsi realizzati: 264;
- Numero Corsisti: 2579;
- Superamento Esame: 98,35%
Contattaci ora per ricevere tutti i dettagli e per richiedere, senza alcun impegno, di parlare direttamente con uno dei nostri Docenti (Clicca qui)
oppure chiamaci subito al nostro Numero Verde (800-177596)
Obiettivi del corso
Di seguito una sintesi degli obiettivi principali del Corso Cisco CCNA:
- Progettare e implementare reti LAN attraverso tecnologie come VLAN, Spanning Tree Protocol, VLAN Trunk Protocol, Etherchannel, HSRP, Switch Port Analyzer, ecc.
- Gestire reti WAN attraverso protocolli di Routing IPv4 e IPv6 come Rip, Eigrp, Ospf, BGP e tecnologie quali PPP, PPPoE, VPN, DMVPN, ecc.
- Monitorare e garantire la sicurezza attraverso NetFlow, SNMP, applicando politiche di QOS e introducendo strumenti come ACL, Firewall, ecc.
- Implementare reti Wireless WLAN utilizzando tecnologie avanzate per soddisfare le esigenze delle realtà produttive medio e grandi.
- Introdurre e applicare reti Programmabili, focalizzandosi sulla Network Programmability nell’ambito del Software Defined Networking (SDN) attraverso casi pratici reali.
Certificazione del corso
Esame CCNA 200-301 – Implementing and Administering Cisco Solutions; La certificazione Cisco CCNA Implementing and Administering Cisco Solutions Esame 200-301 è tra le certificazioni informatiche più richieste al mondo e rappresenta la parte iniziale e fondamentale del programma di certificazioni Cisco, universalmente riconosciuto come il più accreditante nell’ambito del Mercato del Lavoro IT (ICT). Questa certificazione attesta le abilità nell’installazione, configurazione e diagnostica di piccole e medie reti aziendali e di tutti i servizi di networking essenziali indispensabili in ogni contesto produttivo. Il Software Defined Network, la Network Programmability (programmazione delle reti) e i sistemi wireless di tipo enterprise sono tra le nuove competenze testate con questo esame. A partire dal 2020, la certificazione Cisco CCNA rimane l’unica certificazione di livello Associate a precedere i livelli più alti della piramide Cisco
Contenuti del corso
- The importance of the network as a supporting element for all forms of communication.
- Impact of the network in different production realities.
- Devices and technologies used in various business contexts.
- Main trends leveraging networking technologies.
- Key features of the Cisco IOS operating system.
- Basic configurations of Cisco IOS through Command Line Interface (CLI).
- Role of protocols and standards in the development of network technologies.
- Interpretation of Request for Comment (RFC).
- Description of the ISO/OSI and TCP/IP model.
- Comment on the importance of the Level approach.
- Describe the main functions of the levels of the Protocol stack.
- Describe the most important protocols of the Application Level: Http, Https, FTP, Smtp, Pop3, IMAP, Radius, Telnet, TFTP, DNS, etc.
- Role of the Transport Level and in-depth study of TCP and UDP operation.
- Analysis of the fields present in the Segment header.
- Introduction to the Wireshark network analyzer.
- Role of the Network level and in-depth study of IPV4 addressing.
- Analysis of the fields present in the Packet header.
- Types of Unicast, Broadcast, and Multicast traffic.
- Planning of addressing and VLSM Subnetting.
- First concepts of routing and implementation of static routes in different topologies.
- IPV6 protocol differences and in-depth study of operating dynamics.
- Static IPV6 routing applied to different topologies.
- Troubleshooting tools, ICMP, and Traceroute.
- Management, Maintenance, and Backup of Cisco Router and Switch devices.
- In-depth study of IOS Cisco Packaging and Licensing.
- Role of the Data-link level in Lan and Wan contexts.
- In-depth study of the Ethernet protocol.
- Analysis of the fields present in the Frame header.
- Switching technologies, Mac Address, MAC Table, Store and forward cut through.
- Basic configurations of Cisco Switches.
- ARP protocol.
- Types of Transmission Media (UTP, STP, Fiber, Wireless).
- CDP Cisco Discovery Protocol.
- LLDP Link Layer Discovery Protocol.
- NTP Network Time Protocol.
- Notes on the fundamental elements of Computer Security.
- Analysis of the various types of routes available on a router.
- Structure of the IPV4 and IPV6 routing table.
- In-depth study of router decision-making mechanisms.
- Concept of Metric and Administrative Distance.
- Fully Specified IPV4 and IPV6 Static Routes.
- Floating IPV4 and IPV6 Static Routes.
- Routing Lookup Process and difference between RIB and FIB.
- Notes on IP CEF and forwarding technologies.
- Summarization techniques.
- Introduction to dynamic routing.
- Distance-Vector and Link-State routing protocols.
- RIP v1 protocol.
- RIP v2 and RIPng protocol.
- Classfull Vs Classless Protocols.
- EIGRP IPV4 and IPV6 protocol.
- Diffusing Update Algorithm (DUAL).
- Advanced Functions and EIGRP Tuning.
- Auto Summarization and Manual Summarization.
- OSPF and OSPFv3 protocol.
- Shortest Path First (SPF) Algorithm.
- OSPF Tuning.
- OSPF MultiArea: Inter-Area Summarization.
- BGP Border Gateway Protocol.
- Introduction to Access Control List (ACL) IPV4 and IPV6.
- Standard and extended ACL.
- Numbered and named ACL.
- Regulate remote management through ACL.
- ACL management and troubleshooting.
- Network Address Translation.
- Static NAT Static address translation.
- Dynamic NAT Dynamic address translation.
- Port Address Translation (PAT) NAT overloading.
- Port Forwarding.
- NAT64 (notes).
- Level 2 hierarchical network (Core-Distribution-Access level).
- How a switch routes frames. Mac-address table.
- Collision domains and broadcast domains.
- Basic switch configuration.
- Port-security.
- Introduction to VLANs (role of VLANs in a switched network).
- VLAN and trunk configuration.
- Inter-VLAN Routing.
- VTP protocol.
- VLAN Trunk Protocol configuration.
- Introduction to DTP.
- Dynamic Trunking Protocol.
- Inter-vlan routing router on a stick configuration.
- Multi-layer switch.
- Troubleshooting inter-vlan routing.
- Role of the spanning-tree in a switched network with redundancy.
- STP algorithm: switch roles, port roles.
- PVST+ and Rapid PVST+: similarities and differences.
- PVST+ and Rapid PVST+ configuration.
- Link Aggregation in a switched network.
- Link aggregation configuration with Etherchannel.
- Description of FHRP protocols.
- HSRP configuration and troubleshooting.
- Implementation of DHCPv4 in a business network.
- Configuration of a router as a DHCPv4 server and as a DHCPv4 client.
- Implementation of DHCPv6 in a business network.
- DHCPv6 configuration.
- WIRELESS LAN networks: structure of a wireless LAN network.
- Securing a wireless LAN network.
- Configuration of a wireless router.
- Cisco Switch Port Analyzer (SPAN).
- Introduction to WAN networks, differences between LAN and WAN.
- Description of WAN technologies.
- Selecting WAN technologies based on your company’s requirements.
- Difference between public and private WAN.
- HDLC configuration on a point-to-point serial link.
- PPP protocol on a point-to-point serial link.
- PPP configuration.
- PPP authentication configuration (PAP and CHAP).
- PPP troubleshooting.
- Introduction and PPPoE configuration.
- Frame-Relay: how it operates in a business network.
- Frame-Relay configuration.
- Point-to-point subinterface configuration.
- Frame-Relay troubleshooting.
- Introduction to VPN Technologies (SSL and IPsec).
- DMVPN Dynamic Multipoint VPN.
- eBGP iBGP.
- Introduction to QOS.
- Quality of Service configuration.
- Introduction to Syslog, SNMP, and NetFlow and SNMPV3.
- Introduction to Programmable Networks.
- Software Defined Network.
- Cisco ACI (Cisco Application Centric Infrastructure).
- Cisco DNA and WLC.
- Power Over Ethernet (PoE).
- Wi-Fi channels, SSID, RF, and Encryption.
- Components of Wireless architectures (AP, WLC, access, trunk, LAG).
- Management of Access Point and WLC through the main protocols (ssh, https, TACACS+, RADIUS).
- Implementing Qos and advanced WLAN settings.
- Wireless Security (WPA, WPA2, WPA3).
- AAA in the Wireless context.
- Level 2 security (DHCP snooping, dynamic ARP inspection, and port security).
- Comparison between traditional (Legacy) networks and controller-based (SDN) networks.
- Components of the SDN paradigm (overlay, underlay, fabric, control plane, data plane, North-bound, and South-bound APIs).
- Device management through Cisco DNA.
- REST-based APIs (CRUD, HTTP verbs, data encoding).
- Puppet, Chef, Ansible.
- JSON encoded.
Attività Laboratoriali
- Get Started with Cisco Command- Line Interface (CLI)
- Observe How a Switch Operates
- Perform Basic Switch Configuration
- Implement the Initial Switch Configuration
- Inspect TCP/IP Applications
- Configure an Interface on a Cisco Router
- Configure and Verify Layer 2 Discovery Protocols
- Implement an Initial Router Configuration
- Configure Default Gateway
- Explore Packet Forwarding
- Troubleshoot Switch Media and Port Issues
- Troubleshoot Port Duplex Issues
- Configure Basic IPv6 Connectivity
- Configure and Verify IPv4 Static Routes
- Configure IPv6 Static Routes
- Implement IPv4 Static Routing
- Implement IPv6 Static Routing
- Configure VLAN and Trunk
- Troubleshoot VLANs and Trunk
- Configure a Router on a Stick
- Implement Multiple VLANs and Basic Routing Between the VLANs
- Configure and Verify Single- Area OSPF
- Configure and Verify EtherChannel
- Improve Redundant Switched Topologies with EtherChannel
- Configure and Verify IPv4 ACLs
- Implement Numbered and Named IPv4 ACLs
- Configure a Provider- Assigned IPv4 Address
- Configure Static NAT
- Configure Dynamic NAT and Port Address Translation (PAT)
- Implement PAT
- Log into the WLC
- Monitor the WLC
- Configure a Dynamic (VLAN) Interface
- Configure a DHCP Scope
- Configure a WLAN
- Define a Remote Access Dial- In User Service (RADIUS) Server
- Explore Management Options
- Explore the Cisco DNA™ Center
- Configure and Verify NTP
- Configure System Message Logging
- Create the Cisco IOS Image Backup
- Upgrade Cisco IOS Image
- Configure WLAN Using Wi- Fi Protected Access 2 (WPA2) Pre- shared Key (PSK) Using the GUI
- Secure Console and Remote Access
- Enable and Limit Remote Access Connectivity
- Secure Device Administrative Access
- Configure and Verify Port Security
- Implement Device Hardening
Tipologia
Corso di Formazione con Docente
Docenti
I docenti sono Istruttori accreditati CISCO e certificati in altre tecnologie IT, con anni di esperienza pratica nel settore e nella Formazione.
Infrastruttura laboratoriale
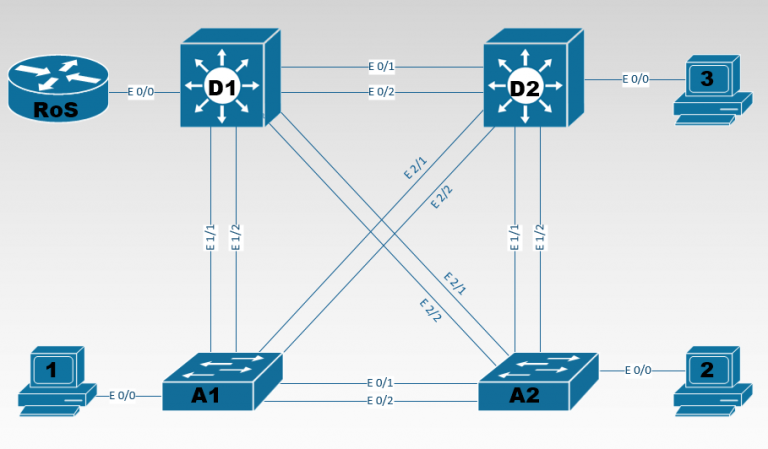
Per tutte le tipologie di erogazione, il Corsista può accedere alle attrezzature e ai sistemi reali Cisco presenti nei Nostri laboratori o direttamente presso i data center Cisco in modalità remota h24. Ogni partecipante dispone di un accesso per implementare le varie configurazioni avendo così un riscontro pratico e immediato della teoria affrontata. Ecco di seguito alcune topologie di rete dei Laboratori Cisco Disponibili:
Dettagli del corso
Prerequisiti
Non ci sono Prerequisiti.
Durata del corso
- Durata Estensiva 120 Ore;
- Durata Intensiva 5gg;
Frequenza
Varie tipologie di Frequenza Estensiva ed Intensiva.
Date del corso
- Corso Cisco CCNA (Formula Intensiva) – 06/05/2024 – 9:00 – 17:00
- Corso Cisco CCNA (Formula Estensiva Serale) – 27/05/2024 – Lun. Mer. 18:30/21:30
- Corso Cisco CCNA (Formula Intensiva) – 08/07/2024 – 9:00 – 17:00
Modalità di iscrizione
Le iscrizioni sono a numero chiuso per garantire ai tutti i partecipanti un servizio eccellente.
L’iscrizione avviene richiedendo di essere contattati dal seguente Link, o contattando la sede al numero verde 800-177596 o inviando una richiesta all’email [email protected].


